NETWRIX STRONGPOINT FOR SALESFORCE
Your first step towards a smarter, safer, Compliant Org
Powerful change management, compliance, and data security tools for Orgs — and businesses — of all sizes
In Salesforce, more customizations mean more risk. But with Strongpoint, businesses can manage change with security and speed. Strongpoint's four product tiers offer progressively deeper alignment with your business practices, so you can document, optimize, administer and audit your Org.
Automate the hardest part of your job
Documentation
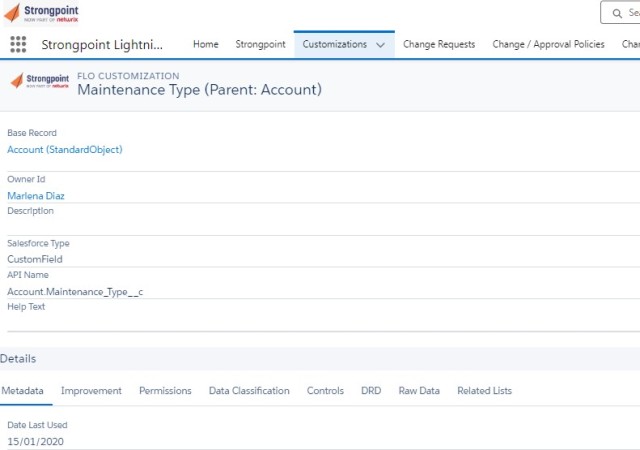
Strongpoint is the only Salesforce-native tool that scans your Org on an ongoing basis and indexes all metadata, and the connections between it. This means you have an accurate, up-to-date record.
Access Management
Netwrix Strongpoint documents and continually monitors your roles, profiles and permission sets. With this data, you can investigate access to critical Objects; troubleshoot access problems; track changes to permissions; create controls to block risky role assignments; and more.
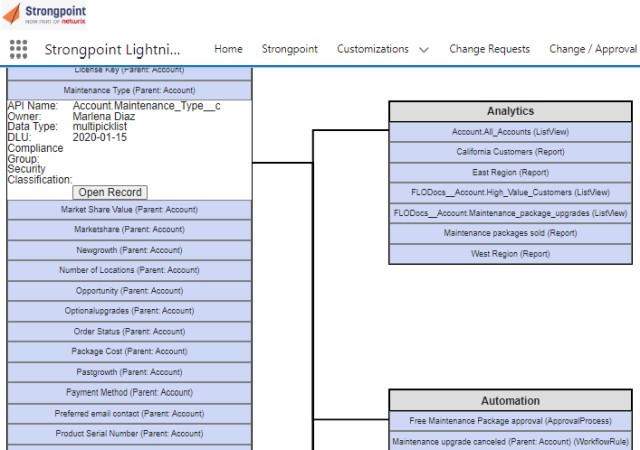
Impact Analysis
Strongpoint gives you tools to see in advance what will happen if you deprecate a field, change a picklist or modify a custom object. Detailed reports show the impact of a potential change, or use our dependency relationship diagrams to see it in an easy-to-understand visual format.
Change Management
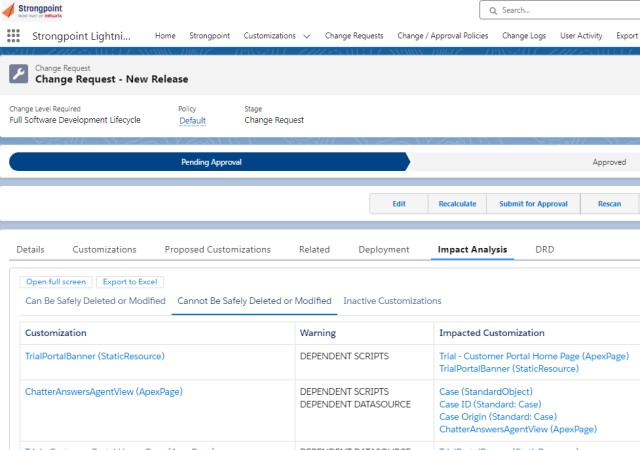
Strongpoint is a true closed-loop Salesforce environment management system. Every change to metadata is captured in an immutable log. Every completed change is reconciled back to an originating request and, if necessary, an approval.
Reporting and Reconciliation
Strongpoint logs every change in your Org, and reconciles change requests and approvals to a verifiable audit log. Out-of-the-box reporting shows you and your auditors what changed, whether or not it was materially significant, and, if it was, who approved it and why.
Configuration Data Management
Strongpoint treats revenue-related data in CPQ, Billing and other apps with the same scrutiny it applies to other Apex metadata in your Org. It is the only native solution that not only gives you visibility into changes to configuration data but also lets you automatically block changes to critical CPQ rules.
Netwrix Strongpoint for Salesforce
Review the datasheet to find out more about how Strongpoint for Salesforce can help you solve many of your challenges.
Netwrix Flashlight for Salesforce
Netwrix Flashlight for Salesforce is a free managed package that automatically documents customizations and the dependencies between them.